Monday, 2 September 2024
South Korea to conduct offensive cyber defence operations to protect national infrastructure from hacking attacks
Friday, 15 December 2023
How risky is it to give card details over the phone and how do I reduce the chance of fraud?
Paul Haskell-Dowland, Edith Cowan University and Ismini Vasileiou, De Montfort University
Paying for things digitally is so common, most of us think nothing of swiping or tapping our card, or using mobile payments. While doing so is second nature, we may be more reluctant to provide card details over the phone.
Merchants are allowed to ask us for credit card details over the phone – this is perfectly legal. But there are minimum standards they must comply with and safeguards to protect consumer data.
So is giving your card details over the phone any more risky than other transactions and how can you minimise the risks?
How is my card data protected?
For a merchant to process card transactions, they are expected to comply with the Payment Card Industry Data Security Standard. This is a set of security requirements designed to protect cardholder data and the trillions of dollars of transactions each year.
Compliance involves various security measures (such as encryption and access controls) together with strong governance and regular security assessments.
If the information stored by the merchant is accessed by an unauthorised party, encryption ensures it is not readable. That means stealing the data would not let the criminals use the card details. Meanwhile, access controls ensure only authorised individuals have access to cardholder data.
Though all companies processing cards are expected to meet the compliance standards, only those processing large volumes are subject to mandatory regular audits. Should a subsequent data leak or misuse occur that can be attributed to a compliance failure, a company can be penalised at levels that can escalate into millions of dollars.
These requirements apply to all card transactions, whether in person, online or over the phone. Phone transactions are likely to involve a human collecting the card details and either entering them into computer systems, or processing the payment through paper forms. The payment card Security Standards Council has detailed guides for best practice:
A policy should be in place to ensure that payment card data is protected against unauthorised viewing, copying, or scanning, in particular on desks.
Although these measures can help to protect your card data, there are still risks in case the details are misplaced or the person on the phone aren’t who they say they are.
Basic tips for safe credit card use over the phone
If you provide card details over the phone, there are steps you can take to minimise the chance you’ll become the victim of fraud, or get your details leaked.
1. Verify the caller
If you didn’t initiate the call, hang up and call the company directly using details you’ve verified yourself. Scammers will often masquerade as a well-known company (for example, an online retailer or a courier) and convince you a payment failed or payment is needed to release a delivery.
Before you provide any information, confirm the caller is legitimate and the purpose of the call is genuine.
2. Be sceptical
If you are being offered a deal that’s too good to be true, have concerns about the person you’re dealing with, or just feel something is not quite right, hang up. You can always call them back later if the caller turns out to be legitimate.
3. Use secure payment methods
If you’ve previously paid the company with other (more secure) methods, ask to use that same method.
4. Keep records
Make sure you record details of the company, the representative you are speaking to and the amount being charged. You should also ask for an order or transaction reference. Don’t forget to ask for the receipt to be sent to you.
Check the transaction against your card matches the receipt – use your banking app, don’t wait for the statement to come through.
Virtual credit cards
In addition to the safeguards mentioned above, a virtual credit card can help reduce the risk of card fraud.
You probably already have a form of virtual card if you’ve added a credit card to your phone for mobile payments. Depending on the financial institution, you can create a new credit card number linked to your physical card.
Some banks extend this functionality to allow you to generate unique card numbers and/or CVV numbers (the three digits at the back of your card). With this approach you can easily separate transactions and cancel a virtual card/number if you have any concerns.
What to do if you think your card details have been compromised or stolen?
It’s important not to panic, but quick action is essential:
call your bank and get the card blocked so you won’t lose any more money. Depending on your situation, you can also block/cancel the card through your banking app or website
report the issue to the police or other relevant body
monitor your account(s) for any unusual transactions
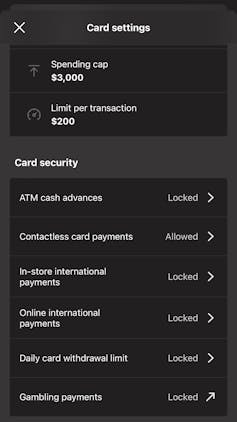
explore card settings in your banking app or website – many providers allow you to limit transactions based on value, restrict transaction types or enable alerts
you may want to consider registering for credit monitoring services and to enable fraud alerts.
So, should I give my card details over the phone?
If you want to minimise risk, it’s best to avoid giving card details over the phone if you can. Providing your card details via a website still has risks, but at least it removes the human element.
The best solution currently available is to use virtual cards – if anything goes wrong you can cancel just that unique card identity, rather than your entire card.![]()
Paul Haskell-Dowland, Professor of Cyber Security Practice, Edith Cowan University and Ismini Vasileiou, Associate Professor, De Montfort University
This article is republished from The Conversation under a Creative Commons license. Read the original article.
Tuesday, 15 December 2020
India bans 43 more Chinese apps

Wednesday, 11 May 2016
Liberty Reserve co-founder sentenced to 20 years in prison
Wednesday, 11 June 2014
China rejects US accusation of cyber attacks

Wednesday, 30 April 2014
Flame Virus: cyber-war spearhead or spyware?

- There are new cyber attacks, it seems that there is an age of cyber warfare approaching very rapidly. But if we look at it from an analytical perspective.
- What kind of political change might the appearance of this complicated and as far as I understand a very expensive creation bring to the local politics? As far as I understand it was in place for the past two years and it is only now being detected. So, does that imply that what we are witnessing now is a total change in the security structures of the world, is my understanding correct? Or perhaps it is also a little bit too alarmist?
- Talking of Russia, what is Russia doing perhaps to increase its own security in this sphere?
Wednesday, 22 January 2014
Students hack school website to skip class
Saturday, 14 September 2013
Cyber warfare is under way
Internet under siege
Monday, 12 August 2013
Americans googling ‘pressure cookers’ end up being questioned by security forces
Saturday, 6 April 2013
Cyber crime: Britain 'lacks skills' to tackle £27bn threat
Thursday, 17 January 2013
Public banned from reading details of Chinese cyber-attack on Google users
Tuesday, 11 December 2012
US Military Train in Cyber-city to Prepare Hack Defence
NEW JERSEY, USA – A miniature "cyber-city" has been created in New Jersey, complete with a bank, hospital, water-tower, train system, power grid and a coffee shop. The buildings are tiny - fitting into an area 6ft (1.8m) by 8ft - but the underlying computer systems mimic those in the real world. The aim is to train US government "cyber-warriors" to fend off attacks. Experts believe attacks on critical infrastructure are likely to become more widespread.Real-world damage Developed in response to a challenge from the US military, the NetWars CyberCity was created by security training organisation the Sans Institute. It will send government hackers on various missions, starting in December. These will include fending off attacks on the city's power company, hospital, water system and transportation services. CyberCity director Ed Skoudis said: "We've built over 18 missions, and each of them challenges participants to devise strategies and employ tactics to thwart computer attacks that would cause significant real-world damage." The missions will typically last between a few hours and a few days.Lose control Sans Institute director Eric Bassel said Greater understanding of a city's vulnerabilities could be critical as computer attacks from nation states became increasingly frequent and sophisticated. "When you lose control of cyberspace, you lose control of the physical world," he said. "We have seen detailed evidence of foreign nations deep inside the computer networks of our financial services companies, manufacturing companies and critical infrastructure," Mr Bassel added. Such attacks had been going on for many years, he said, but efforts to fight them off had been limited. "With NetWars CyberCity we hope to turn the tables by providing our first-line cyber-defenders with the necessary skills and hands-on training to fend off online attacks and regain control of cyberspace," he added. For security consultant Alan Woodward, such cities perform a vital job. "Dotted around Salisbury Plain there are loads of deserted villages that the army now uses for training, and this is the cyber-equivalent," he said. He said such mock-ups would become increasingly sophisticated but would always be limited. "All it will do is teach you have to defend and respond to a situation but it will never prevent attacks," he said. Source: BBC News, Source: Koreaittimes
Wednesday, 31 October 2012
Govt to invest $200 million in 4 years on cyber security
Wednesday, 26 September 2012
US hacker says iPhone 5 jailbroken
Saturday, 22 September 2012
Three Russians involved in Internet scam in US
By: Vesnovskaya Maria, The US police have found out that three Russians were involved (not two as it was earlier reported) in a confidence game with the fake sale of cars via the Internet across the US. The investigators discovered that the man who was put in prison in California and produced a German passport was actually a Russian citizen.In total six people were arrested in case of the car sale scam and all of them come from the post-Soviet countries. The swindlers used popular websites such as eBay Motors, Auto Trader, Yahoo Auto and Craigslist for placing fake advertisements for cars for sale. Clients were asked to transfer deposits for the cars to the accounts of PayPal and eBay pay systems, where the money was to be kept until the deal was closed. Once a client made his choice that sum was to be transferred to the account of the car dealers. But in reality once the money was transferred to the accounts of the pay systems, the swindlers withdrew it in small amounts and transferred those sums to their accounts in Europe. The shysters managed to play the con-game for 3 years and-a-half and made more than $4 million. Читать далее, Source: Voice of Russia.
Saturday, 8 September 2012
Dawn of global cyberwar
Thursday, 26 July 2012
Twitter users given legal warning in Britain
after admitting a racially aggravated public order offence. Some 17 arrests have been made in connection with the alleged naming on Twitter of the woman that Wales footballer Ched Evans was last month convicted of raping. In March, former New Zealand cricketer Chris Cairns won a libel action against ex-Indian Premier League chairman Lalit Modi in the first libel action heard in England against a post on Twitter. Judge David Bean dismissed fixing allegations levelled against the cricketer by Modi, leaving Madi facing a bill of more than USD 800,000. Grieve said the government did not need to create new laws as existing ones already make it illegal to "grossly offend" or "cause distress" Source; Financial Express
Tuesday, 17 July 2012
Warning about online fraud as information theft rises





Saturday, 9 June 2012
China to tighten Internet control with new rules






.jpg)
